
最近看到大佬们玩这个,感觉很厉害的样子,我也学习了一下怎么用这个东西。
Ocserv也就是OpenConnect,即Cisco AnyConnect的兼容服务端。
AnyConnect目前支持 Windows 7+ / Android / IOS / Mac ,其他设备没有客户端所以无法使用,例如 XP系统。
这个主要是我在debian8上安装的时候的步骤。
安装步骤
检查PPP/TUN环境
cat /dev/net/tun # 返回的必须是: cat: /dev/net/tun: File descriptor in bad state
安装依赖
apt-get install pkg-config build-essential libgnutls28-dev libwrap0-dev liblz4-dev libseccomp-dev libreadline-dev libnl-nf-3-dev libev-dev gnutls-bin -y
编译安装
然后我们新建一个文件夹,并下载和编译安装 ocserv,此处用的 ocserv 可能不是最新的,最新的请看:ocserv
mkdir ocserv && cd ocserv wget ftp://ftp.infradead.org/pub/ocserv/ocserv-0.12.5.tar.xz tar -xJf ocserv-0.12.5.tar.xz && cd ocserv-0.12.5 ./configure make make install # 安装后的文件可以不删除,卸载的时候还需要用到。
最后我们新建一个配置文件的文件夹:
mkdir /etc/ocserv wget -N --no-check-certificate -P "/etc/ocserv" "https://files.zorz.cc/ocserv.conf"
上面下载的是doub.io大佬根据 ocserv 默认配置文件稍微改了改以适应教程的配置文件。
如果你想要自己改配置文件可以去看源码默认自带的配置文件: ocserv-0.11.9/doc/sample.config
配置参数解释
auth = "plain[passwd=/etc/ocserv/ocpasswd]" # 这个是登陆方式,plain[passwd=/etc/ocserv/ocpasswd] 代表使用密码登陆并且从 /etc/ocserv/ocpasswd 文件中读取用户名和密码 # listen-host = [IP|HOSTNAME] # 这个代表监听的IP或主机名,注释掉即可。 tcp-port = 443 udp-port = 443 # 这个代表 TCP和UDP监听的端口 默认443,如果端口被干扰或被占用,可以更换其他端口,端口号可分开 server-cert = /etc/ocserv/ssl/server-cert.pem server-key = /etc/ocserv/ssl/server-key.pem ca-cert = /etc/ocserv/ssl/ca-cert.pem # 服务器证书和CA证书的位置 banner = "Hello World" # 欢迎文本,链接上VPN后,客户端会提示这个消息,不需要注释即可。 max-clients = 16 # 整个VPN最大链接客户端数量 max-same-clients = 2 # 同账号链接VPN最大客户端数量 rekey-method = ssl # 加密方式 SSL pid-file = /var/run/ocserv.pid # PID(记录进程PID)文件位置 device = vpns # 设备名(随意) ipv4-network = 192.168.1.0 ipv4-netmask = 255.255.255.0 #ipv4-network = 192.168.1.0/24 #ipv6-network = fda9:4efe:7e3b:03ea::/48 tunnel-all-dns = true # 是否接管DNS解析请求到VPN服务器,true代表客户端的DNS请求全部又服务器处理。 dns = 8.8.8.8 dns = 8.8.4.4 # 服务端的DNS # route = 10.10.10.0/255.255.255.0 # route = 192.168.0.0/255.255.0.0 # route = fef4:db8:1000:1001::/64 # route = default # no-route = 192.168.5.0/255.255.255.0 # 路由表相关的,不是很懂,据说是可以用来分流国内外流量,但是最多64条太少了。 # 使ocserv兼容AnyConnect cisco-client-compat = true
添加VPN用户
假设你要添加的账号用户名为hello,那么命令如下:
ocpasswd -c /etc/ocserv/ocpasswd hello
输入后,服务器会提示你输入两次密码(不会显示,盲输),如下:
# === 服务器输出示例 === # root@debian:~/ocserv/ocserv-0.11.8# ocpasswd -c /etc/ocserv/ocpasswd hello Enter password: Re-enter password: # === 服务器输出示例 === #
删除 VPN用户
注意:删除/锁定/解锁 VPN用户都没有任何提示!
ocpasswd -c /etc/ocserv/ocpasswd -d hello
锁定 VPN用户
ocpasswd -c /etc/ocserv/ocpasswd -l hello
解锁 VPN用户
ocpasswd -c /etc/ocserv/ocpasswd -u hello
自签SSL证书
首先在当前目录新建一个文件夹(要养成不把文件乱扔的习惯)。
mkdir ssl && cd ssl
生成 CA证书
然后用下面的命令代码(8行一起复制一起粘贴一起执行),其中的两个 hello 可以随意改为其他内容,不影响。
echo -e 'cn = "hello" organization = "hello" serial = 1 expiration_days = 365 ca signing_key cert_signing_key crl_signing_key' > ca.tmpl
然后我们生成证书和密匙:
certtool --generate-privkey --outfile ca-key.pem certtool --generate-self-signed --load-privkey ca-key.pem --template ca.tmpl --outfile ca-cert.pem
生成服务器证书
继续用下面的命令代码(6行一起复制一起粘贴一起执行),其中的 1.1.1.1 请改为你的服务器IP,而 hello 可以随意改为其他内容,不影响。
echo -e 'cn = "1.1.1.1" organization = "hello" expiration_days = 365 signing_key encryption_key tls_www_server' > server.tmpl
然后我们生成证书和密匙:
certtool --generate-privkey --outfile server-key.pem certtool --generate-certificate --load-privkey server-key.pem --load-ca-certificate ca-cert.pem --load-ca-privkey ca-key.pem --template server.tmpl --outfile server-cert.pem
最后我们在ocserv的目录中新建一个ssl文件夹用于存放证书。
mkdir /etc/ocserv/ssl
把刚才生成的证书和密匙都移过去:
mv ca-cert.pem /etc/ocserv/ssl/ca-cert.pem mv ca-key.pem /etc/ocserv/ssl/ca-key.pem mv server-cert.pem /etc/ocserv/ssl/server-cert.pem mv server-key.pem /etc/ocserv/ssl/server-key.pem
现在刚才在当前文件夹新建的 ssl 文件夹就没用了,你可以删除它:cd .. && rm -rf ssl/
安装服务
1、下载doub.io大佬写好的服务脚本并赋予执行权限:
wget -N --no-check-certificate -O "/etc/init.d/ocserv" "https://files.zorz.cc/ocserv_debian" chmod +x /etc/init.d/ocserv
设置开机启动(可选)
update-rc.d -f ocserv defaults
2、支持systemd的系统(debian8/ubuntu16.04及以上):
如果你的系统支持systemd的话,那么不用执行上面的命令,使用下面的命令即可。
ln -s /usr/local/sbin/ocserv /usr/sbin/ocserv cp /root/ocserv/ocserv-0.12.5/doc/systemd/standalone/ocserv.service /etc/systemd/system/
设置开机启动(可选)
systemctl enable ocserv
开启IPv4转发
sed -i '/net.ipv4.ip_forward.*/d;$a\net.ipv4.ip_forward = 1' /etc/sysctl.conf sysctl -p
配置防火墙
iptables -t nat -A POSTROUTING -j MASQUERADE iptables -I INPUT -p tcp --dport 443 -j ACCEPT iptables -I INPUT -p udp --dport 443 -j ACCEPT iptables -A FORWARD -p tcp --tcp-flags SYN,RST SYN -j TCPMSS --clamp-mss-to-pmtu
这么设置了防火墙之后,重启就会失效,为了使防火墙规则持久化,执行以下操作
iptables-save > /etc/iptables.rule
输入crontab -e文件,添加以下内容
@reboot /sbin/iptables-restore < /etc/iptables.rule
最后测试
ocserv -f -d 1 # 如果没有问题,那么我们就按 Ctrl + C 键退出。
使用说明
service ocserv start # 启动 ocserv service ocserv stop # 停止 ocserv service ocserv restart # 重启 ocserv service ocserv status # 查看 ocserv 运行状态 service ocserv log # 查看 ocserv 运行日志 service ocserv test # 测试 ocserv 配置文件是否正确
配置文件:/etc/ocserv/ocserv.conf
假设你一开始源码编译安装的目录是:/root/ocserv/ocserv-0.11.8 ,那么这么做:
cd /root/ocserv/ocserv-0.11.8 # 进入源码编辑安装目录 make uninstall # 执行卸载命令 cd .. && cd .. rm -rf ocserv/ # 回到 /root 文件夹,删除 ocserv 源码自身 rm -rf /etc/ocserv/ # 删除配置文件目录
如果你还下载了系统服务脚本并设置开机启动了,那么需要:
rm -rf /etc/init.d/ocserv update-rc.d -f ocserv remove
路由表
由于ocserv默认是全局,可以通过配置/etc/ocserv/ocserv.conf的方式来指定国内流量直连,国外流量走ocserv。但是这种方法并不总是有效的。
moeclub.org大佬的路由表,使用 no-route 方式.
须将 $YourIP 替换为服务器地址,否则将会连不上服务器.
将以下内容添加到ocserv.conf文件的最后
## No Route List no-route = $YourIP/255.255.255.255 no-route = 192.168.0.0/255.255.0.0 no-route = 1.0.0.0/255.192.0.0 no-route = 1.64.0.0/255.224.0.0 no-route = 1.112.0.0/255.248.0.0 no-route = 1.176.0.0/255.240.0.0 no-route = 1.192.0.0/255.240.0.0 no-route = 14.0.0.0/255.224.0.0 no-route = 14.96.0.0/255.224.0.0 no-route = 14.128.0.0/255.224.0.0 no-route = 14.192.0.0/255.224.0.0 no-route = 27.0.0.0/255.192.0.0 no-route = 27.96.0.0/255.224.0.0 no-route = 27.128.0.0/255.224.0.0 no-route = 27.176.0.0/255.240.0.0 no-route = 27.192.0.0/255.224.0.0 no-route = 27.224.0.0/255.252.0.0 no-route = 36.0.0.0/255.192.0.0 no-route = 36.96.0.0/255.224.0.0 no-route = 36.128.0.0/255.192.0.0 no-route = 36.192.0.0/255.224.0.0 no-route = 36.240.0.0/255.240.0.0 no-route = 39.0.0.0/255.255.0.0 no-route = 39.64.0.0/255.224.0.0 no-route = 39.96.0.0/255.240.0.0 no-route = 39.128.0.0/255.192.0.0 no-route = 40.72.0.0/255.254.0.0 no-route = 40.124.0.0/255.252.0.0 no-route = 42.0.0.0/255.248.0.0 no-route = 42.48.0.0/255.240.0.0 no-route = 42.80.0.0/255.240.0.0 no-route = 42.96.0.0/255.224.0.0 no-route = 42.128.0.0/255.128.0.0 no-route = 43.224.0.0/255.224.0.0 no-route = 45.65.16.0/255.255.240.0 no-route = 45.112.0.0/255.240.0.0 no-route = 45.248.0.0/255.248.0.0 no-route = 47.92.0.0/255.252.0.0 no-route = 47.96.0.0/255.224.0.0 no-route = 49.0.0.0/255.128.0.0 no-route = 49.128.0.0/255.224.0.0 no-route = 49.192.0.0/255.192.0.0 no-route = 52.80.0.0/255.252.0.0 no-route = 54.222.0.0/255.254.0.0 no-route = 58.0.0.0/255.128.0.0 no-route = 58.128.0.0/255.224.0.0 no-route = 58.192.0.0/255.224.0.0 no-route = 58.240.0.0/255.240.0.0 no-route = 59.32.0.0/255.224.0.0 no-route = 59.64.0.0/255.224.0.0 no-route = 59.96.0.0/255.240.0.0 no-route = 59.144.0.0/255.240.0.0 no-route = 59.160.0.0/255.224.0.0 no-route = 59.192.0.0/255.192.0.0 no-route = 60.0.0.0/255.224.0.0 no-route = 60.48.0.0/255.240.0.0 no-route = 60.160.0.0/255.224.0.0 no-route = 60.192.0.0/255.192.0.0 no-route = 61.0.0.0/255.192.0.0 no-route = 61.80.0.0/255.248.0.0 no-route = 61.128.0.0/255.192.0.0 no-route = 61.224.0.0/255.224.0.0 no-route = 91.234.36.0/255.255.255.0 no-route = 101.0.0.0/255.128.0.0 no-route = 101.128.0.0/255.224.0.0 no-route = 101.192.0.0/255.240.0.0 no-route = 101.224.0.0/255.224.0.0 no-route = 103.0.0.0/255.0.0.0 no-route = 106.0.0.0/255.128.0.0 no-route = 106.224.0.0/255.240.0.0 no-route = 110.0.0.0/255.128.0.0 no-route = 110.144.0.0/255.240.0.0 no-route = 110.160.0.0/255.224.0.0 no-route = 110.192.0.0/255.192.0.0 no-route = 111.0.0.0/255.192.0.0 no-route = 111.64.0.0/255.224.0.0 no-route = 111.112.0.0/255.240.0.0 no-route = 111.128.0.0/255.192.0.0 no-route = 111.192.0.0/255.224.0.0 no-route = 111.224.0.0/255.240.0.0 no-route = 112.0.0.0/255.128.0.0 no-route = 112.128.0.0/255.240.0.0 no-route = 112.192.0.0/255.252.0.0 no-route = 112.224.0.0/255.224.0.0 no-route = 113.0.0.0/255.128.0.0 no-route = 113.128.0.0/255.240.0.0 no-route = 113.192.0.0/255.192.0.0 no-route = 114.16.0.0/255.240.0.0 no-route = 114.48.0.0/255.240.0.0 no-route = 114.64.0.0/255.192.0.0 no-route = 114.128.0.0/255.240.0.0 no-route = 114.192.0.0/255.192.0.0 no-route = 115.0.0.0/255.0.0.0 no-route = 116.0.0.0/255.0.0.0 no-route = 117.0.0.0/255.128.0.0 no-route = 117.128.0.0/255.192.0.0 no-route = 118.16.0.0/255.240.0.0 no-route = 118.64.0.0/255.192.0.0 no-route = 118.128.0.0/255.128.0.0 no-route = 119.0.0.0/255.128.0.0 no-route = 119.128.0.0/255.192.0.0 no-route = 119.224.0.0/255.224.0.0 no-route = 120.0.0.0/255.192.0.0 no-route = 120.64.0.0/255.224.0.0 no-route = 120.128.0.0/255.240.0.0 no-route = 120.192.0.0/255.192.0.0 no-route = 121.0.0.0/255.128.0.0 no-route = 121.192.0.0/255.192.0.0 no-route = 122.0.0.0/254.0.0.0 no-route = 124.0.0.0/255.0.0.0 no-route = 125.0.0.0/255.128.0.0 no-route = 125.160.0.0/255.224.0.0 no-route = 125.192.0.0/255.192.0.0 no-route = 137.59.59.0/255.255.255.0 no-route = 137.59.88.0/255.255.252.0 no-route = 139.0.0.0/255.224.0.0 no-route = 139.128.0.0/255.128.0.0 no-route = 140.64.0.0/255.240.0.0 no-route = 140.128.0.0/255.240.0.0 no-route = 140.192.0.0/255.192.0.0 no-route = 144.0.0.0/255.248.0.0 no-route = 144.12.0.0/255.255.0.0 no-route = 144.48.0.0/255.248.0.0 no-route = 144.123.0.0/255.255.0.0 no-route = 144.255.0.0/255.255.0.0 no-route = 146.196.0.0/255.255.128.0 no-route = 150.0.0.0/255.255.0.0 no-route = 150.96.0.0/255.224.0.0 no-route = 150.128.0.0/255.240.0.0 no-route = 150.192.0.0/255.192.0.0 no-route = 152.104.128.0/255.255.128.0 no-route = 153.0.0.0/255.192.0.0 no-route = 153.96.0.0/255.224.0.0 no-route = 157.0.0.0/255.255.0.0 no-route = 157.18.0.0/255.255.0.0 no-route = 157.61.0.0/255.255.0.0 no-route = 157.112.0.0/255.240.0.0 no-route = 157.144.0.0/255.240.0.0 no-route = 157.255.0.0/255.255.0.0 no-route = 159.226.0.0/255.255.0.0 no-route = 160.19.0.0/255.255.0.0 no-route = 160.20.48.0/255.255.252.0 no-route = 160.202.0.0/255.255.0.0 no-route = 160.238.64.0/255.255.252.0 no-route = 161.207.0.0/255.255.0.0 no-route = 162.105.0.0/255.255.0.0 no-route = 163.0.0.0/255.192.0.0 no-route = 163.96.0.0/255.224.0.0 no-route = 163.128.0.0/255.192.0.0 no-route = 163.192.0.0/255.224.0.0 no-route = 164.52.0.0/255.255.128.0 no-route = 166.111.0.0/255.255.0.0 no-route = 167.139.0.0/255.255.0.0 no-route = 167.189.0.0/255.255.0.0 no-route = 167.220.244.0/255.255.252.0 no-route = 168.160.0.0/255.255.0.0 no-route = 170.179.0.0/255.255.0.0 no-route = 171.0.0.0/255.128.0.0 no-route = 171.192.0.0/255.224.0.0 no-route = 175.0.0.0/255.128.0.0 no-route = 175.128.0.0/255.192.0.0 no-route = 180.64.0.0/255.192.0.0 no-route = 180.128.0.0/255.128.0.0 no-route = 182.0.0.0/255.0.0.0 no-route = 183.0.0.0/255.192.0.0 no-route = 183.64.0.0/255.224.0.0 no-route = 183.128.0.0/255.128.0.0 no-route = 192.124.154.0/255.255.255.0 no-route = 192.140.128.0/255.255.128.0 no-route = 202.0.0.0/255.128.0.0 no-route = 202.128.0.0/255.192.0.0 no-route = 202.192.0.0/255.224.0.0 no-route = 203.0.0.0/255.0.0.0 no-route = 210.0.0.0/255.192.0.0 no-route = 210.64.0.0/255.224.0.0 no-route = 210.160.0.0/255.224.0.0 no-route = 210.192.0.0/255.224.0.0 no-route = 211.64.0.0/255.248.0.0 no-route = 211.80.0.0/255.240.0.0 no-route = 211.96.0.0/255.248.0.0 no-route = 211.136.0.0/255.248.0.0 no-route = 211.144.0.0/255.240.0.0 no-route = 211.160.0.0/255.248.0.0 no-route = 216.250.108.0/255.255.252.0 no-route = 218.0.0.0/255.128.0.0 no-route = 218.160.0.0/255.224.0.0 no-route = 218.192.0.0/255.192.0.0 no-route = 219.64.0.0/255.224.0.0 no-route = 219.128.0.0/255.224.0.0 no-route = 219.192.0.0/255.192.0.0 no-route = 220.96.0.0/255.224.0.0 no-route = 220.128.0.0/255.128.0.0 no-route = 221.0.0.0/255.224.0.0 no-route = 221.96.0.0/255.224.0.0 no-route = 221.128.0.0/255.128.0.0 no-route = 222.0.0.0/255.0.0.0 no-route = 223.0.0.0/255.224.0.0 no-route = 223.64.0.0/255.192.0.0 no-route = 223.128.0.0/255.128.0.0
本次学习的内容大概就是这样,主要内容来自:doub.io 和 moeclub.org.
补充:
Windows客户端
anyconnect-win-4.6.01103-core-vpn-predeploy-k9
注意:使用自签证书时链接服务器时会无法链接,请在设置里面将Block connections to untrusted servers前的复选框去掉。

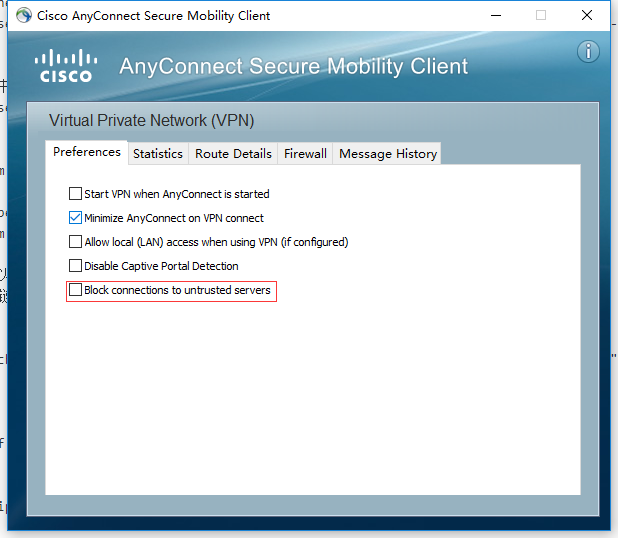
这样设置之后重新链接即可,链接时会出现警告,继续即可。
当然,你也可以看我另外一篇文章:可信SSL证书版ocserv
